Accessories for the Paranoid uses fake data to stop your devices spying on you
Katja Trinkwalder and Pia-Marie Stute have designed a series of add-on accessories for those who are concerned about surveillance and their data security.
The project, called Accessories For The Paranoid, explores an alternative approach to data security through four different "parasitic" objects.
These include a webcam that projects fabricated scenes and a button that generates fake online data.
These objects work to block or thwart the collection of people's user information in different ways by generating fake data to blur their digital profiles, hiding users' true data identities behind "a veil of fictive information".

"When you consider data as the oil of the 21st century, each of us is sitting on a small ground treasure – a resource that is being discretely mined by the most valuable companies in the world," said the designers.
"As users of modern services and products, we have long become habituated to trade-offs in which 'free' services are offered in exchange for some bits of our personal data."

The internet of things has introduced a new kind of object into our homes that depend on collecting this information.
These products are able to observe the users, learn from their observations and then make their own decisions without further human interference.
"With the comfort of automation also comes a subtle danger in our connected devices, which process personal information about their users every day," said the Cologne-based designers.
"If attempts to restrict the flow of our personal data would consequentially restrict our access to said services and products as well, do we have no other option but to obey and share?" they asked.

The first object in the series is the "un-hacking" webcam, which takes the principle of a toy camera and applies it to data security by displaying different, fabricated scenes through the webcam as if it was in real-time.
The webcam addresses fears of hackers gaining access to the cameras positioned at the top of users' laptops or smart devices, allowing them to see into their personal spaces.

The second object is an add-on to the well-known Amazon Echo virtual assistant, which responds to the call of "Alexa".
Having to listen at all times in order to detect the call of its name, the Alexa device observes, processes and collects data in the user's home whenever it is switched on.
Trinkwalder and Stute's design aims to prevent the user's sensitive information from being heard either by fitting onto the top of the device and "numbing" Alexa when needed, or by feeding fake information to the device.
For the latter, users can choose between three modes to play over the voiceover.
These are white noise that lets no information slip through, pre-recorded quests to occupy Alexa with useless tasks, or dialogues from random movie scenes that make the device collect fake information about the user and their surroundings.
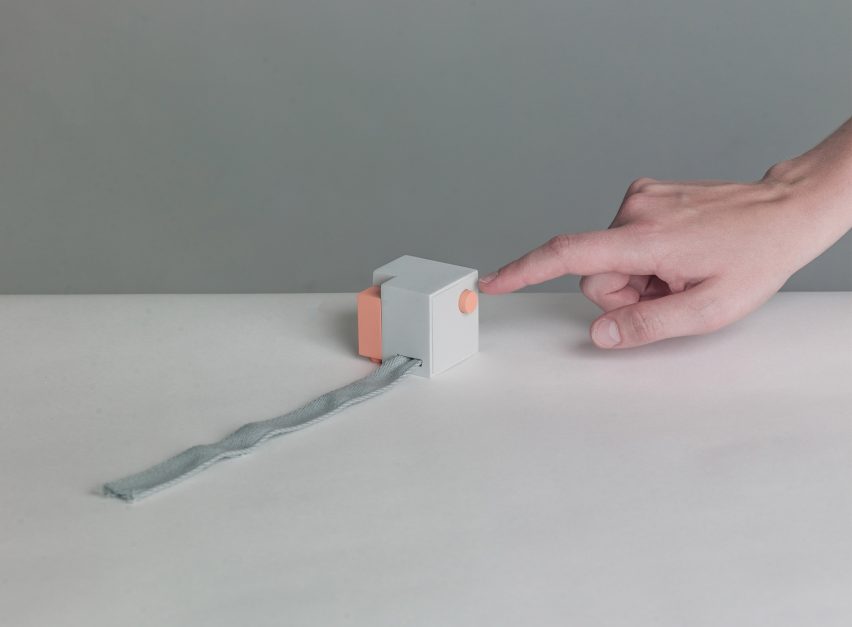
Connected to any computer, the third object in the series will generate fake online data.
By pushing the button, an algorithm will randomly create site-specific content on the websites of services such as Google, Facebook, YouTube, Twitter or Amazon.
Once the browser has been opened, this object will access a popular service and leave fault digital traces. A wish-list on Amazon will be filled with unexpected interests, for instance, or a post on twitter will be completed through random emojis replacing keywords.
The user's Facebook account could also spread indefinite likes, while on Google search, partially typed requests will be continued through the google auto-completion.

The final object in the collection can be connected to any device able to collect data. It aims to blur people's use patterns by randomly pushing the buttons of the device it's attached to when activated.
This then creates fake user patterns when the user sleeps during night time, or when they're not at home.
While none of these prototype products can be bought, they act as a demonstration of the common desire to protect our privacy.
Gadi Amit's studio New Deal Design showed a similar goal when it collaborated with tech start-up Helm to create a home server that allows users to take control of their data security.